A tale of how not to do it, with a happy ending.
Our hunting club has eight Kenwood TK-2000 walkie-talkies. This is hardly ever enough, even when I take my Baofeng UV-B5* with.
So when a fellow ham had two TK-2000s for sale, I bought them. The programming cable is easy, and the software (KPG-137D) is not hard to find.
The first radio programmed fine, the second one… is password protected. I’m sure there’s a trick to resetting the password, I just don’t know what it is. So out comes the schematic from the service manual, and there’s an EX24016 hanging off the side of the R5F2136A microcontroller. EX24016 being another way of saying 24C16 which is an EEPROM. Memory. Where things get stored.
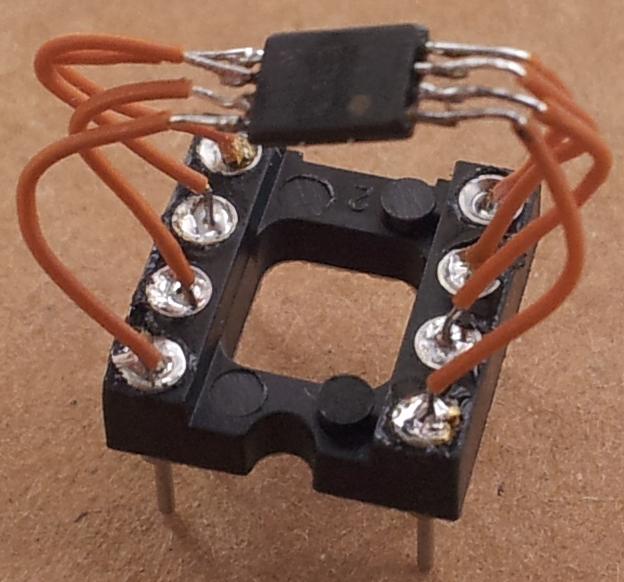
And while my favourite programming language is not solder, I’m not half bad at it.
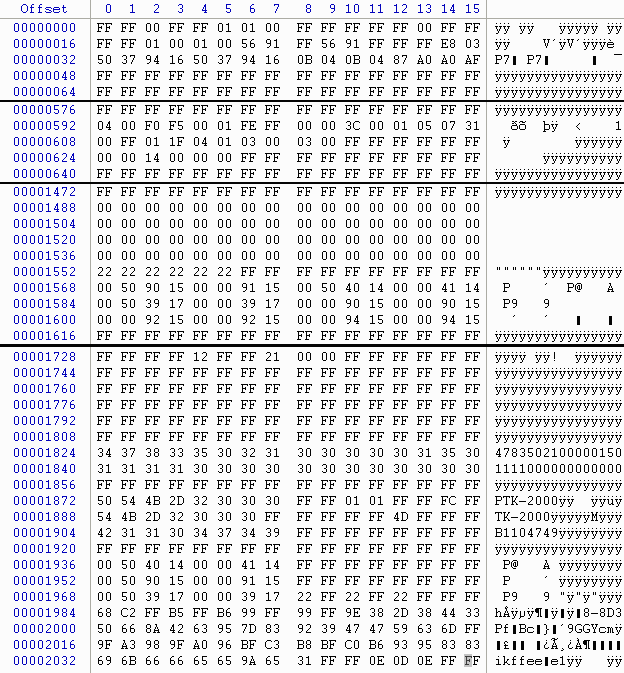
And one universal programmer and one of my favourite tools later we have (the bits not shown are all just FF).
OK, so what does this mean? Stumped me too. The stuff at the end is self-explanatory, it’s a TK-2000 and the serial number of this one is B1104749. I’m pretty sure it’s on the same frequency as the other one, that would be one channel only, 169.43750 with a 103.5 Hz subtone, high power, narrow band. Oh look, right at the start there’s a sequence of bytes, 50 37 94 16 repeated twice. Back to front, transmit and receive frequencies. Given enough time one could decipher the whole thing, but that’s not important right now. We need the password.
The KPG-137D help file tells me that there are two passwords, one to allow you to read the data and the other for writing. The password is a number from zero to 999999 (six digits). This eliminates a whole bunch of hopefuls like “PTK-2000” or one of those long strings at 1824/1840.
So I stuck the EEPROM back into the radio, wired the cable up, and started guessing. I had some hope for “222222”, for example. But no, it wasn’t going to be that easy.
So I thought, maybe the KPG-137D software “knows” what the password is. In other words, is the password sent to the transceiver, or checked on the local machine? I’m not expecting strong security here. I wired a second serial port to eavesdrop on the datastream (19200 N81) and saw that there’s no traffic on the line while I’m guessing passwords. So I tried looking on the heap of the KPG-137D but I suspect the password is stored as a number, not as text, no joy there either. There’s a lot of data on the heap and anything could be the password. Someone who knows Windows better than I do would be able to trap this thing at the right place and get the password.
Next I hauled out my working transceiver, and eavesdropped the datastream with different passwords set (I started with 000000, 000001, 000002). I noticed that the first 52 bytes of a read are the same and that after that things change.
Password Bytes 53-56 Binary
000000 AC B3 AF AD 1010 1100 1011 0011 1010 1111 1010 1101
000001 B8 A7 BB B9 1011 1000 1010 0111 1011 1011 1011 1001
000002 A9 B6 AA A8 1010 1001 1011 0110 1010 1010 1010 1000
^^^ ^ ^ ^^^ ^ ^ ^^^ ^ ^ ^^^ ^ ^
Note the columns that stay the same in the binary. This suggests that old favourite, XOR encryption. The only problem is that I’m changing two bits in the password and three bits are changing in the data, which suggests some other nefarious seekrit manipulation.
With enough sample cases, I can figure it out, I’m sure.
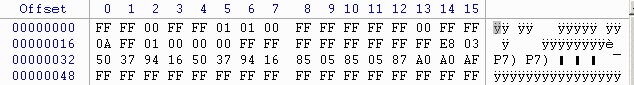
Time to try something else. I didn’t really want to potentially break my working transceiver, but desperate times. Yup, I ripped the EEPROM out of that sucker and read it as well.
Byte 16 is “0A” instead of “FF” and bytes 22/23 and 25/26 is “FF FF” instead of “56 91”. That’s the first difference in the EEPROM, might as well start there. I first converted 0x5691 and 0x9156 to decimal, that didn’t work, but plain old “5691” did. I would have put money on “9156” being more likely to work than “5691”, based on the frequency being stored arse-endian, but no.
So there you have it. If I’d tried enough numbers from the EEPROM instead of giving up after not finding the password in plain text, I would have been there a lot earlier.
* A cheap and nasty, but extremely versatile little radio. Does VHF and UHF amateur bands, PMR and FRS, marine… you can get yourself into all kinds of trouble with this thing.